THANK YOU FOR SUBSCRIBING
Editor's Pick (1 - 4 of 8)

Strengthen Cyber Defences Through Culture Change
Steve Williamson, Audit Account Director, Security and Data Privacy, GSK (GSK: LON)


Steve Williamson, Audit Account Director, Security and Data Privacy, GSK (GSK: LON)
Similarly, a secure-coding challenges (with a leader board), where developers create an avatar, choose their programming language, identify source code vulnerabilities and select the best alternative code-block, introduces fun and competitiveness. It is the characteristics of fun, challenge and competitiveness that make gamification-based learning engaging, and the lessons learned from these games stick with the individuals and carry forward into their day-to-day jobs.
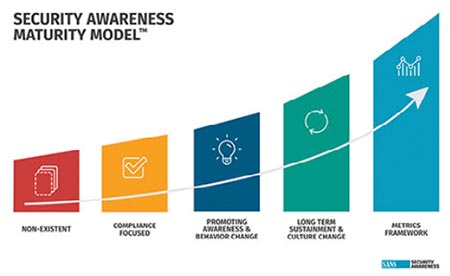
The SANS Security Awareness Maturity Model (see below) is a powerful benchmarking tool, which can help organisations to quickly determine why their security awareness programme may not be having the impact they want. On a 5-point scale, Level 2 means an organisation is meeting its Legal and Compliance obligations through mandatory training. For Level 3, content is communicated in an engaging and positive manner that encourages behaviour change. Level 4 is characterised by a strong security minded culture, which is built into almost all operational aspects of the organisation.
The need to develop a strong security culture is increasingly recognised as a high priority for many organisations. Culture can be thought of as the attitudes, beliefs and behavioural norms of employees within an organisation. It is exhibited through Behaviours, Attitudes to compliance, Communications and Responsibilities. For example, if someone accidentally emails a sensitive file to unauthorised individuals external to the organisation, a positive security behaviour would be for the individual to promptly self-report the incident to ensure corrective action can be taken (which may include notification to impacted parties or regulatory bodies). A strong awareness of responsibilities with respect to data protection is another cultural dimension. Individuals should always know the classification level of the information they are handling and should be aware that they are responsible for its security, especially when it needs to be shared with others. A positive behavioural norm would be to grant access only on a need to know basis, minimise copies and delete files when they are no longer required.
 Conclusion
In today’s hyper-connected world, organisations build their cyber defence using layers of safeguards covering People, Process and Technology. Data breaches and cyber-attacks often arise from human behaviour. Social engineering, especially phishing, is a highly effective tactic which gives the attacker a foothold in the network, and data loss incidents are most frequently caused by human error. Therefore, to build a strong cyber defence, organisations should have a Security Awareness Programme targeted at creating a security conscious culture. Such a programme needs to be engaging, continuous and relevant to the job roles, and would likely include gamification, culture assessments and management metrics.
Conclusion
In today’s hyper-connected world, organisations build their cyber defence using layers of safeguards covering People, Process and Technology. Data breaches and cyber-attacks often arise from human behaviour. Social engineering, especially phishing, is a highly effective tactic which gives the attacker a foothold in the network, and data loss incidents are most frequently caused by human error. Therefore, to build a strong cyber defence, organisations should have a Security Awareness Programme targeted at creating a security conscious culture. Such a programme needs to be engaging, continuous and relevant to the job roles, and would likely include gamification, culture assessments and management metrics.
In Today’s Hyper-Connected World, Organisations Build Their Cyber Defence Using Layers of Safeguards Covering People, Process and Technology
 Conclusion
In today’s hyper-connected world, organisations build their cyber defence using layers of safeguards covering People, Process and Technology. Data breaches and cyber-attacks often arise from human behaviour. Social engineering, especially phishing, is a highly effective tactic which gives the attacker a foothold in the network, and data loss incidents are most frequently caused by human error. Therefore, to build a strong cyber defence, organisations should have a Security Awareness Programme targeted at creating a security conscious culture. Such a programme needs to be engaging, continuous and relevant to the job roles, and would likely include gamification, culture assessments and management metrics.
Conclusion
In today’s hyper-connected world, organisations build their cyber defence using layers of safeguards covering People, Process and Technology. Data breaches and cyber-attacks often arise from human behaviour. Social engineering, especially phishing, is a highly effective tactic which gives the attacker a foothold in the network, and data loss incidents are most frequently caused by human error. Therefore, to build a strong cyber defence, organisations should have a Security Awareness Programme targeted at creating a security conscious culture. Such a programme needs to be engaging, continuous and relevant to the job roles, and would likely include gamification, culture assessments and management metrics.












